This should be a common scenario in shared housing worldwide: you’ve got one Internet connection coming into the house, into a router shared among two or more chumps. Chumps A and B each have an Xbox 360. Specifically, Chump A has one that sounds like an aircraft engine turbine – courtesy of Microsoft’s repair centre. Both chumps want to connect to Xbox Live at the same time and play some Rainbow Six Vegas. Unlike most other games, R6V should not be played under the influence of alcohol: it’s enraging enough playing it sober.
With most consumer routers sold today, this scenario should “automagically” work through the wonders of UPnP (Universal Plug n’ Play). This technology provides a method to forward ports through a NAT firewall based on a device request. In a standard PC setting, you might see this used for uTorrent or other P2P applications. Unfortunately, the wizard has failed to enchant my personal setup, and both chumps A and B experience a disconnection after about 20 minutes of gameplay. The disconnect is really more of a fraudulent excuse, as both chumps can reconnect immediately after receiving the message.
For some background as to why this issue occurs, it’s important to note that Xbox Live needs certain ports forwarded properly for an “Open” connection (best chance of matching). TCP 3074, UDP 3074 and UDP 88. Only one Xbox can open this set of ports at a time:
Xbox A (192.168.1.100) > Internal Port 3074 > Router > External Port 3074 > Xbox Live
Once this mapping is set in the UPnP table, no other system can occupy external port 3074. So the Xbox Live software picks another port in a similar range to communicate with Xbox Live:
Xbox B (192.168.1.101) > Internal Port 3074 > Router > External Port 3641 > Xbox Live
UPnP mapping unfortunately can run into conflicts if an Xbox loses its DHCP lease, or the mapping fails to be renewed on a regular basis. During this time, the external port mapping can “flip”, leaving Xbox B getting data from port 3074 instead of the alternately chosen 3641. In short, Xbox B gets the packets meant for Xbox A, causing the ‘heartbeat’ packets to Live to fail out. The result is an abrupt disconnection.
It’s not possible to merely set a static IP address for each Xbox: UPnP relies on the DHCP server in the router handing out addresses. If you set static addresses, your connection will be listed as “Moderate” NAT for at least one of your consoles.
We’ve replicated this problem on both the latest versions of Tomato and DD-WRT, running on a Linksys WRT54GL.
The Solution
Using either one of these alternate firmwares, a function called “Static DHCP” becomes available. In essence, it lets you provide a MAC address for a computer or other Ethernet-enabled device. When the network card in question attempts to get a DHCP lease for an IP address, the Static DHCP table takes over and will always assign the same IP address to the same device. This process has all the benefits of setting a static address, without having to change Windows or console settings.
What you’ll want to do is find your console’s MAC address. In Tomato and DD-WRT, you can likely find the device with an OUI code that matches Microsoft. DD-WRT provides this information in the Status > LAN tab.
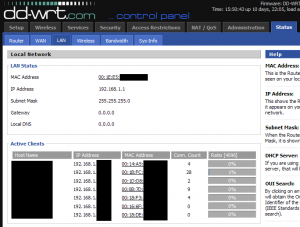
Tomato provides the active connections in Status > Device List. (You can click directly on the IP address to copy the associated MAC into the static DHCP table.)
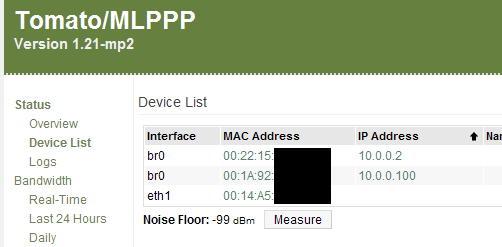
Alternatively, you can look up the MAC address on the Xbox following these instructions (the process is still similar for systems running the NXE.)
Once you have the console MAC address, click over to the Services tab in DD-WRT, or the Basic > Static DHCP section in Tomato. In DD-WRT, click the Add button if there are no more fields available. You’ll want to provide the Xbox MAC address and a new IP address – something below your normal DHCP range (usually 192.168.1.100 onward.) For example, we’ve picked 192.168.1.40 and 192.168.1.41 for two Xbox consoles.
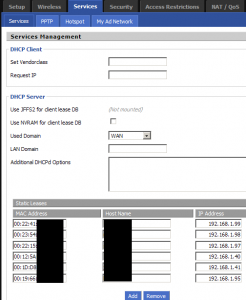
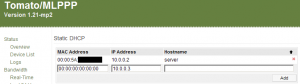
Once you’re done making these changes in Tomato, remember to click the Save button at the bottom of the page. DD-WRT users should first click Save, and then Apply Settings when the page reloads.
Finally, return to Status > LAN (DD-WRT) or Status > Device List (Tomato) and remove any dynamic DHCP entries in the 192.168.1.100+ range for the consoles. Save and apply your settings, then go reboot the Xbox consoles and run a network test. It should pick up the new IP address and work properly for any Xbox Live activity.
Congratulations! No more random disconnections, unless Xbox Live falls down like it did last Christmas. 🙂










